Hacking ZXHN H108N router and accessing the shell as root through Telnet, how to use Python to build your own tool and perform a brute-force attack.
Part One: Shell over Telnet
Hello good people.
I was playing around with the ZXHN H108N (ZTE) for quite a while now, and to be honest, I have a lot to talk about here, but in this article, the topic is hacking ZXHN H108N router to access the shell, using the Telnet connection.
Note: part two can be found here: ZXHN H108N Router Web-Shell and Secrets.
Note: Telnet port must be open for this scenario to work, usually port 23 is open for LAN connections, and filtered/close for WAN connection, also it is worth to mention that all the scripts below can run on both Linux/Unix, and Windows machines.
Access Points (Wireless Home Routers) as you may already know provide lots of services, such as DHCP, DNS, Wireless connection, Firewall, and so on, these services must run on top of an OS, which is usually Linux, in fact I don’t know of an AP that runs on something different (if you disagree, please comment it down), the scenario here will describe my story step-by-step on how I managed to get root access to the OS, so this is not a tutorial, this is my story, my personal experience.
Please note that I am by no means a ZTE tech. guru, and as I mentioned before, I was just “curious”.
Disclaimer: I shall not be held liable to and shall not accept any liability, obligation or responsibility whatsoever for any loss or damage may be caused by applying or implementing the attacks and/or commands describe hereunder. The information provided here is for educational purpose only, and you are not allowed to use any of these techniques to attack or even probe others, which if done, by-low this can be considered a crime.
This tutorial was written in June 2014, and posted somewhere else (including on my old blog), I reviewed everything and fixed some errors, I also created new scripts and hosted them online for public use.
Scanning for Open Ports
So, first thing to do is to scan the ports, detect the OS and get any other information available, for that I usually use nmap, but first let us see my connection information (as proper information gathering should be), please note that I am on a Linux machine, nevertheless I will explain how to get the same results on Windows machine when applicable.
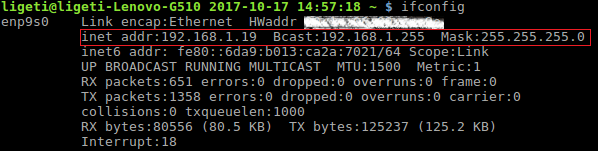
First, get the IP address using ifconfig command:
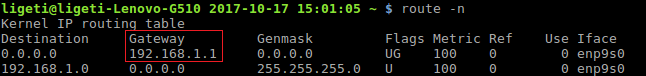
Then get the gateway address:
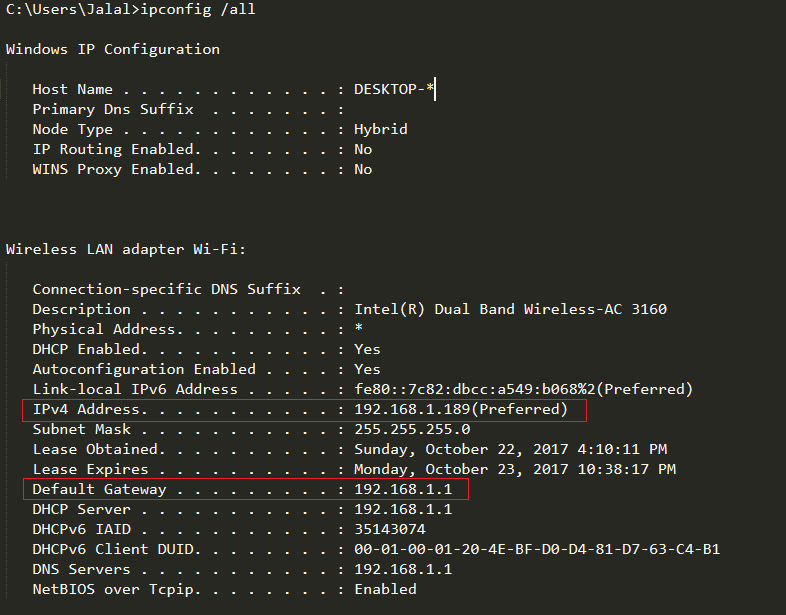
So, our target/gateway is on 192.168.1.1 (not the case always, so it is always a good idea to check), under Windows machine, to get the same results, as you may already know, you can use the ipconfig command (one command to reveal both the IP and Gateway addresses):
All the above is basic stuff…
Port scanning:
I used a fast scan (-F option) for no reason really… well maybe just to make it faster, but a proper information gathering should check all ports (TCP and UDP). The -O flag is for OS detection (for more information about nmap command, please visit: https://nmap.org/docs.html)
As we can see in the results above, the OS is Linux 2.6.9-30 and there are three ports opened, one of them is port 23/tcp telnet, whenever I see telnet available I think to myself “This should be fun!” and it was!
Gaining Access
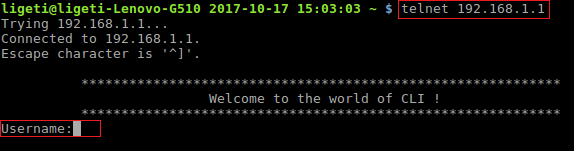
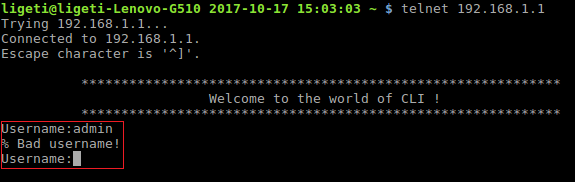
The next thing is to try and connect to the router using a Telnet client (if you are on Windows you should install it first by going to Control Panel > Programs and Features > Turn Windows feature on or off, anyway, here is the result from my first attempt to connect:
We need the username and password to access the CLI (Command Line Interface), I just tried couple of random usernames, and I discovered that I had 3 attempts before the connection is closed by the host.
The first test was “admin”, and it returned “% Bad username!” but then I thought to myself: “If I want to access the shell as root… the username should be root, right? duh!!!”, so I tried root and it was correct.
As for the password I tried couple of known passwords such as toor, root, admin, admin123…etc. none worked (I failed), and I got “% Bad password!” message.
I could go on for hours/days/weeks… but I want to access the shell and I wanted NOW!!! And yes, I am impatient, sorry about that… I guess!
Hacking ZXHN H108N Router by Brute-Force
So, what do we have so far?
- IP address (gateway: 192.168.1.1)
- Telnet access (TCP/23)
- Username: root
- “% Bad password!” message.
I need the password, with a cup of coffee with crème, and no sugar please!
After I got over my depression which took me a while, I decided to write my own script (in Python) to crack the password.
<Brain-Screwing> The reason why I didn’t use Hydra-THC is because… well, you may not like this, but a great man (a Guru?... I guess) his name is Swami Chinmayananda, once said: “… reaching the ideal is not the goal. striving to reach it, that is the moment when you grow.”, may sound irrelevant, but this what I believe, reaching the goal is not my goal! But what I learn from trying to reach it is my goal… Note: if you are reading this in the morning, I sincerely apologize for any brain damage I might’ve caused, that’s why I always highly recommend having a big cup of Irish coffee while reading my blog… 😐 </Brain-Screwing>
Back to Earth (or wherever you are now), using dictionary attack, I used a very small wordlist, the wordlist (or dictionary) is made of the most common used passwords, I don’t remember where I got this list from (I think it was from SQLMAP or Kali, but it is not important really as you can use any wordlist out there available for free on the web (or build your own dictionary… a much better approach).
Important to know that I edited the wordlist file to have only low characters, 3 to 6 characters long and doesn’t have a repeated character more than twice.
The Code
You can download the script from here: https://github.com/Ligeti15/ZXHN-H108N-Login/blob/master/ZXHN-Telnet-Cracker.py
<Brain-Screwing> Note: the script is dirty, I know that, and I don’t really care, all I want is the password, if you don’t like it, have a banana, but please don’t fire back on me in the comments section, because… sigh, I am too old, and too tired, believe me, you don’t want to read my medical history, the medieval period of European history has less events than my medical history… 😐 </Brain-Screwing>
So here is a sample output:
Bingo! The password is “public”, note that I cheated in the above test, because the original run took me over 10 hours and I forgot to take a snapshot… so yes, that happened!
OK, time to test:
Explanation:
- Connect to 192.168.1.1:23 (telnet).
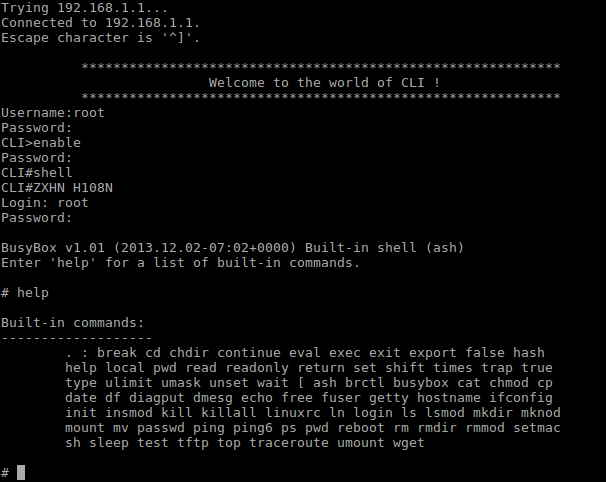
- Enter the user name and password (root/public).
- The prompt will change to CLI> which is similar to Cisco routers, so I try ‘?’ for help.
- I see enable command, which switch the CLI to Privileged Commands Mode.
Access to the Config Mode
I still need the password to enable the config mode, I tested some random passwords manually, and I guessed it successfully after few attempts, BUT… let’s try brute-force the damn thing anyway.
The password is alphanumeric, so my charset will be:
>>> string.ascii_letters + string.digits ‘abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789’
So, I need a code to test the combination of all these letters … crazy eh? Because the total tries for only three characters password would be:
>>> pow(len(string.ascii_letters + string.digits), 3) 238328
And for 8 characters:
>>> pow(len(string.ascii_letters + string.digits), 8) 218340105584896L
I have no time for this … so I will show you a simple script (just for fun), that will check only 3
characters long passwords (and only with string.lowercase charset).
The Code
The script can be found here: https://github.com/Ligeti15/ZXHN-H108N-Login/blob/master/ZXHN-Enable-Mode-Cracker.py
Note: took me a long time (hours) to crack, but in the snapshot below I did a trick to accelerate things enormously.
Yes, it was ‘zte’, something I did guess by myself (of course, you don’t believe me? Strange… because I never lie!!!), and with this information I could access the config mode:
I don’t want to make this article any longer, I know that the subject is kind of boring (add to that my rusty sense of humor), but… I had to share it, and for a very good reason.
Finally, and what you were waiting for maybe, the username and the password for the shell is root:root (was tested manually).
Final Notes
The common Vulnerabilities and Exposure (CVE) database, has a large list of critical vulnerabilities found in ZTE products, the ZXHN AP has multiple vulnerabilities.
ZTE announced that they closed all the vulnerabilities found in the ZXHN, the question is, did your ISP push the patches?
The vulnerability I am exploiting in this article is CVE-2015-7251
You can find a list of all the vulnerabilities found in the ZXHN here: https://www.cvedetails.com/vulnerability-list/vendor_id-11971/product_id-32820/version_id-188244/ZTE-Zxhn-H108n-R1a-Firmware-Zte.bhs.zxhnh108nr1a.h-Pe.html
A list of all the vulnerabilities in ZTE products can be found here: https://www.cvedetails.com/vulnerability-list/vendor_id-11971/ZTE.html
Summary
So, hacking ZXHN H108N router is simple:
- We connected to the router (192.168.1.1) using telnet.
- Authentication process was in place.
- We managed to guess the username, and cracked the password using a dictionary (using the tool I scripted in Python).
- Then we found out that there is more to dig into, so we enabled the configuration mode.
- Again we need to login (another authentication process), this time we brute-forced the password and gain access.
- Last but not the least, we guessed (easily) the username and password used to access the shell as root!
Conclusion
If your router is using Telnet, get another one! If it does use SSH check the version and security configuration, be very careful with these issues, a misconfigured network device can be the worst nightmare one can have if a hacker finds out about it, you should always check and double check your network configuration and devices you use.
Thank you and please leave your comments or questions.
Ligeti








Dear God!
So simple passwords!
So exposed!
My brand new router (gift from my ISP) is a ZXHN H267N.
I am wondering now if I should thank them or not…
On the bright side, my previous router seemed to be worse.
Plus, they seem to have either changed the telnet port or disabled it in this version.
I will dig a bit more into that…
But I am seriously thinking of using a second router in double-NATing mode to protect me, just in case.
Plus, I want to put a public server in the” DMZ” between the two routers.
At least, if someone hacks the router or the server, MAYBE they fail to pass through my second router (DSL-N14U) which seems better in terms of security, although there is an exploit for it that is pretty ridiculous: https://www.exploit-db.com/exploits/43900.
The things that I see make me wonder if they leave these security holes on purpose.
The first web site that I wrote at university had better security that these things!
You mean translate?
Hello! Do you allow me to post this tutorial in Brazil?
Excellent work Thank you very much
chi mi può recuperare una password di un router tp – link
SSID: TP-LINK_6A08 MAC ADDRESS: 1E:8B:CA:C6:6A:08
What if telnet port 23 is closed, like on mine ZTE MF83M? How do I open this port and Can I do it with port forwarding because it seems not to work.
Hi
Are you sure you have the same version? same model?
enable or shell part doesn’t work in mine !!
the password was admin … and it doesn’t ask for username !
k
enable or shell part doesn’t work in mine !!
the password was admin … and it doesn’t ask for username !
Usually I don’t say this, but I do NOT recommend using this router, problem is that it’s cheap, so ISPs prefer it over good quality, and if you read the second part you will see many back-doors, web-shell for example, which is something that I totally disrespect.
Thank you for sharing this information, I highly appreciate it.
Thanks,
Jalal
Hey thanks for the info, I want to inform any TTNET customers who checks this website for getting an idea to hack this rooter since it’s very buggy and some security reasons.
TTNET ZTE H108N rooter için, telnet port:23 k.adı:admin şifre:ttnet, enable dedikten sonra şifre:zte
Hello
when i Access in telnet mode and enter any command his say
%invalid input detected at ‘^’ marker
and if enter command like : lan
% incomplete command
what do in the problem
waiting you reply ???
Hello.
Thanks for the answer, actually I think my ADSL provider had changed this username, because this modem have internal files modified so the provider can easily help users configure the connection, etc.
Only the shell is unacessible. I was wishing I could access it so I can find any config file to disable the auto-redirect the H108N does when the phone cable is disconnected (I’m using it as a port-binded router).
Sorry for bad english. It would be of big help if I could access the shell.
Hello Michel
Did you try to access the web-shell and check available users from there? here is the link to the article that explain how to access the web-shell: https://jalalsela.com/zxhn-h108n-router-web-shell-secrets/
Also, I recommend to check your frameware version, maybe it is patched, as I mentioned in my article, these vulnerabilities were patched by ZTE.
Also, recently I hacked another ZTE router, the username and password were admin/admin (not an ZXHN H108N module), maybe you need to run a brute-force attack to -at least- enumerate the available users, I already explained the issues with “Wrong username” error message, you can use that to enumerate the users.
Please let me know if you need more details or assistance, and sorry about the late response.
Thanks
Hello.
I followed yours tips, but when I arrived on the shell step, the user is not root or admin or whatever.
Firstly, How can I discover the right username? Can you help me?
Pingback: ZXHN H108N Router Web-Shell and Secrets | Jalal Sela
Thank you, I will indeed, there are lots of them that I am currently reviewing, thank you for your kind feedback and support, I really appreciate it.
Excellent! Please do more tutorials